what is BigAnt??
BigAnt is instant messenger that features a 128bit encrypted messages and send files, clearly structured on-line list of users, and easier to use. BigAnt used on client computers with server computers.
BigAnt is instant messenger that features a 128bit encrypted messages and send files, clearly structured on-line list of users, and easier to use. BigAnt used on client computers with server computers.
fuzzer same as before, but this time we are trying to fuzzing "USV" owned by BigAnt. Run BigAnt application with ollydbg make script fuzzing as below, and running
after fuzzing run it will appear as below, where the fuzzer trying to send a buffer of 2500 into the BigAnt
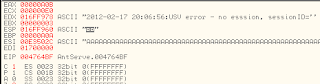
BigAnt crash, but EIP address not directly affected by the buffer is sent, for look into the SEH choose view-->SEH chain, so will display as below
and then press shift+f9, as below
Now EIP address is 41414141, after that try to see data in the aplication memory, right-click at stack line --> Follow in Dump, so will as below
after that find the location command POP, POP, RETN, from ollydbg --> view -->Executable Modules --> double click at vbajet32.dll,
after that get into window CPU from file vbajet32.dl
right-click --> search for --> Sequence of Command and input POP32, POP 32, RETN, as picture below
and click find, the result as below
after that find the pattern create to overwrite SEH,
after get offset, copy the offset to script and modify script as below
and then run the fuzzer, after show the result choose view-->SEH chain and press shift+f9 and will show as below
after that used pattern offset to get the value of EIP
after get the value modify script
save and run again the fuzzer, so will show as below
after that, modify the script again where we input offset address vbajet32.dll
after as above then press shift+f9, the result as below
after that right-click at first address \xCC (012FFD7C) Follow in Dump --> Selection
and the result as below
after that find the payload with msfweb
input as needed, for bad character input from last searching
copy the payload to script, and modify script as below























Tidak ada komentar:
Posting Komentar