prepare file which will be used as a tool to buffer overflow,
save and generate that file. after that download from window virtual
after download, load file "galau.ram" from RM-MP3, but before it, running RM-MP3 from ollydbg
so will seen file of affected, likes under this
after that, write command "pattern_create.rb 27000 > string_create.txt", open file "string_create.txt" and copy to the console
load again in RM-MP3 with ollydbg, and will show likes under this
after that input ESP and EIP at pattern_offset, so that we can know how many bytes are needed to reach the stack,
and change in the console file galau, and i try to change EIP with variable DEADBEEF used little-endian
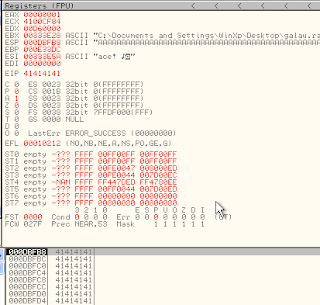
save and load again file "galau.ram", and will show likes under this, look value of EIP change to DEADBEEF
after that i try to doing writing at ESP, add command likes under this
and the result seen likes under this
and then i search the JMP ESP with ollydbg, way as shown below
so will show window likes under this, and i choose shell32.dll

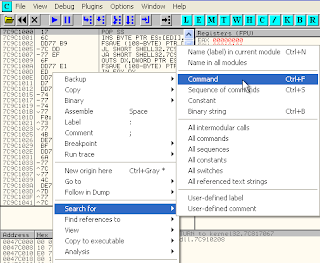
right-click and choose "seacrh for --> Command"
and write "JMP ESP" at window that appears
so i get the JMP ESP address
and then modify the script again
and load the file again so will transform likes under this
well find the payload using metasploit, in this season i used windows bind shell, and setting as needed
and i get the payload
copy payload in the script made earlier
load again file galau.ram and will sees likes under this
it denotes the application crash, and finally write "telnet <ip_target> <port>"
and finally i get into virtual windows system




















Tidak ada komentar:
Posting Komentar